Ahoy !
I opened this new thread to mention apps where reconfig and addition needed to recompile to work againg together
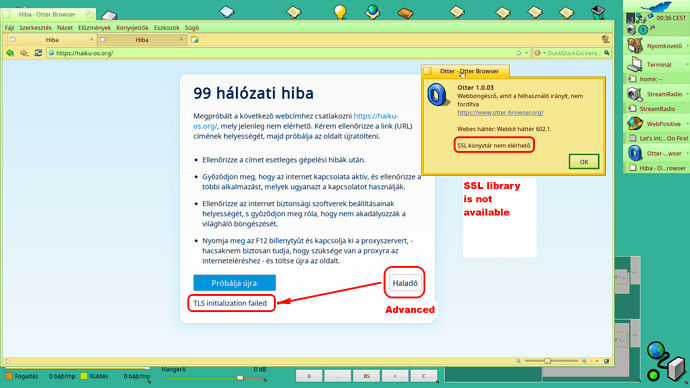
with upgraded TLS/SSL version.
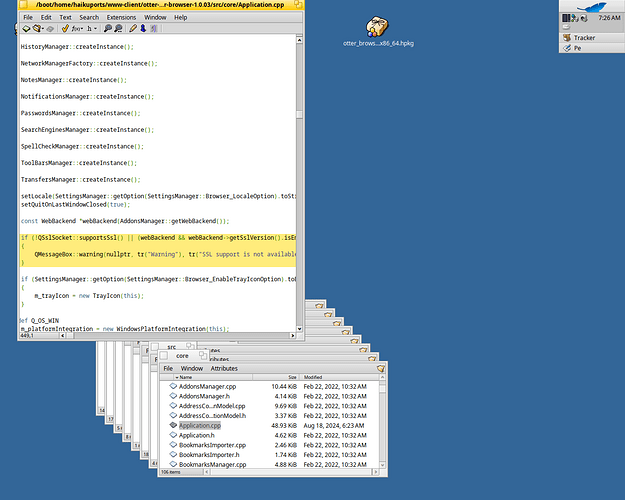
As OpenSSL v1.1 lifecycle has ended - on Haiku - it was resolved by intruducing a backward compatible, but newer openssl 3.x version.
It was followed on many packages but
there are more that had not scoped closely by the OS itself
and / or
especially all other ported or 3rd party applications running on Haiku (32 and 64 bit either).
I thought I open this thread and someone who has a Github account and (would) use that application can report there as well - ( just as ) the maintainer(s) may not follow the forum posts.
Actually I accept developers decision to use Github for reporting issues of such apps
but , at the same time , I still do not want create an account … just for that reporting.
I am not a developer, so I do not need and want to have that account so far.
These issues can be experienced , at this moment .
on Nightly (master branch)
and / or
on the shaping new beta (r1beta5 branch)
Thanks in advance for your acceptance and understanding –
… especially those ones who are going to / would immediately propose the opening an issue about it on Github.
For them I kindly ask to read again the opening post. (THIS ONE :)) )