I think that’s the idea in the virtio stack (and in the “new driver model” in general). The low-level driver is specific to PCI, but then all layers above can be generic and reused easily (hopefully).
VirtIO driver registration working:
PANIC: did not find any boot partitions!
Welcome to Kernel Debugging Land...
Thread 14 "main2" running on CPU 0
Stack:
FP: 0xcd099a40, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0xcd099ab0, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0xcd099af0, PC: <kernel_riscv64> panic + 93
FP: 0xcd099f70, PC: <kernel_riscv64> vfs_mount_boot_file_system + 821
FP: 0xcd099fc0, PC: <kernel_riscv64> _ZL5main2Pv + 283
FP: 0xcd099fe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
initial commands: dm_tree
(0) @0x00000000813afe60 "system/devices_root/driver_v1" (ref 31, init 28, module 0x00000000803d3730, data 0x0000000000000000)
"device/pretty name" : string : "Devices Root"
"device/bus" : string : "root"
"device/flags" : uint32 : 6 (0x6)
"device/driver" : string : "system/devices_root/driver_v1"
(1) @0x00000000813afdc0 "bus_managers/fdt/root/driver_v1" (ref 27, init 24, module 0x000000008078d240, data 0x0000000081262690)
"device/pretty name" : string : "FDT"
"device/flags" : uint32 : 4 (0x4)
"device/driver" : string : "bus_managers/fdt/root/driver_v1"
(2) @0x00000000813afd20 "bus_managers/fdt/driver_v1" (ref 33, init 22, module 0x000000008078d2a8, data 0x0000000081023630)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 0 (0x0)
"fdt/name" : string : ""
"fdt/compatible" : string : "ucbbar,riscvemu-bar_dev"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(3) @0x00000000813af000 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x00000000813b5b10)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1664 (0x680)
"fdt/name" : string : "chosen"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(3) @0x00000000813af960 "bus_managers/fdt/driver_v1" (ref 34, init 15, module 0x000000008078d2a8, data 0x0000000081023250)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 548 (0x224)
"fdt/name" : string : "soc"
"fdt/compatible" : string : "ucbbar,riscvemu-bar-soc"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(4) @0x00000000813af0a0 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x00000000813b5b80)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1496 (0x5d8)
"fdt/name" : string : "framebuffer@41000000"
"fdt/compatible" : string : "simple-framebuffer"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(4) @0x00000000813af1e0 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x00000000813b5c30)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1400 (0x578)
"fdt/name" : string : "virtio@40014000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af140 "busses/virtio/virtio_mmio/driver_v1" (ref 2, init 1, module 0x00000000809c2db0, data 0x0000000081049440)
"device/pretty name" : string : "Virtio MMIO"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 18 (0x12)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(4) @0x00000000813af320 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x00000000813b5d20)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1304 (0x518)
"fdt/name" : string : "virtio@40013000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af280 "busses/virtio/virtio_mmio/driver_v1" (ref 2, init 1, module 0x00000000809c2db0, data 0x00000000810494a0)
"device/pretty name" : string : "Virtio MMIO"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 18 (0x12)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(4) @0x00000000813af460 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x00000000813b5df0)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1208 (0x4b8)
"fdt/name" : string : "virtio@40012000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af3c0 "busses/virtio/virtio_mmio/driver_v1" (ref 2, init 1, module 0x00000000809c2db0, data 0x0000000081049500)
"device/pretty name" : string : "Virtio MMIO"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 2 (0x2)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(4) @0x00000000813af5a0 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x00000000813b5ef0)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1112 (0x458)
"fdt/name" : string : "virtio@40011000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af500 "busses/virtio/virtio_mmio/driver_v1" (ref 2, init 1, module 0x00000000809c2db0, data 0x0000000081049560)
"device/pretty name" : string : "Virtio MMIO"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 1 (0x1)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(4) @0x00000000813af6e0 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x0000000081023010)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1016 (0x3f8)
"fdt/name" : string : "virtio@40010000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af640 "busses/virtio/virtio_mmio/driver_v1" (ref 2, init 1, module 0x00000000809c2db0, data 0x00000000810495c0)
"device/pretty name" : string : "Virtio MMIO"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 3 (0x3)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(4) @0x00000000813af780 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x0000000081023090)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 920 (0x398)
"fdt/name" : string : "serial@10000000"
"fdt/compatible" : string : "ns16550a"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(4) @0x00000000813af820 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x0000000081023130)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 756 (0x2f4)
"fdt/name" : string : "plic@40100000"
"fdt/compatible" : string : "riscv,plic0"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(4) @0x00000000813af8c0 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x00000000810231b0)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 648 (0x288)
"fdt/name" : string : "clint@2000000"
"fdt/compatible" : string : "riscv,clint0"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(3) @0x00000000813afa00 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x00000000810232d0)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 508 (0x1fc)
"fdt/name" : string : "htif"
"fdt/compatible" : string : "ucb,htif0"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(3) @0x00000000813afaa0 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x0000000081023350)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 436 (0x1b4)
"fdt/name" : string : "memory@80000000"
"fdt/device_type" : string : "memory"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(3) @0x00000000813afc80 "bus_managers/fdt/driver_v1" (ref 6, init 3, module 0x000000008078d2a8, data 0x0000000081023530)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 112 (0x70)
"fdt/name" : string : "cpus"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(4) @0x00000000813afbe0 "bus_managers/fdt/driver_v1" (ref 5, init 2, module 0x000000008078d2a8, data 0x0000000081023460)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 172 (0xac)
"fdt/name" : string : "cpu@0"
"fdt/device_type" : string : "cpu"
"fdt/compatible" : string : "riscv"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813afb40 "bus_managers/fdt/driver_v1" (ref 2, init 1, module 0x000000008078d2a8, data 0x00000000810233f0)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 324 (0x144)
"fdt/name" : string : "interrupt-controller"
"fdt/compatible" : string : "riscv,cpu-intc"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(1) @0x00000000813b9f08 "system/devices_generic/driver_v1" (ref 3, init 2, module 0x00000000803d36d0, data 0x0000000000000000)
"device/pretty name" : string : "Generic"
"device/bus" : string : "generic"
"device/flags" : uint32 : 7 (0x7)
"device/driver" : string : "system/devices_generic/driver_v1"
Existing Haiku virtio_block driver attached. Not working yet because of not implemented VirtIO driver interface.
(4) @0x00000000813af460 "bus_managers/fdt/driver_v1" (ref 6, init 3, module 0x000000008078d2a8, data 0x00000000813b5d90)
"device/bus" : string : "fdt"
"fdt/node" : uint32 : 1208 (0x4b8)
"fdt/name" : string : "virtio@40012000"
"fdt/compatible" : string : "virtio,mmio"
"device/driver" : string : "bus_managers/fdt/driver_v1"
(5) @0x00000000813af3c0 "busses/virtio/virtio_mmio/driver_v1" (ref 4, init 2, module 0x00000000809c2e08, data 0x0000000081049500)
"device/pretty name" : string : "Virtio MMIO"
"device/bus" : string : "virtio"
"virtio/version" : uint32 : 2 (0x2)
"virtio/device_id" : uint32 : 2 (0x2)
"virtio/type" : uint16 : 2 (0x2)
"virtio/vendor_id" : uint32 : 65535 (0xffff)
"device/driver" : string : "busses/virtio/virtio_mmio/driver_v1"
(6) @0x00000000813af320 "drivers/disk/virtual/virtio_block/driver_v1" (ref 2, init 1, module 0x00000000809bf340, data 0x00000000813b7cb0)
"device/driver" : string : "drivers/disk/virtual/virtio_block/driver_v1"
"dev/5/path" : string : "disk/virtual/virtio_block/0/raw"
"dev/5/driver" : string : "drivers/disk/virtual/virtio_block/device_v1"
device: drivers/disk/virtual/virtio_block/device_v1, 0x0000000000000000
So the Haiku software engineering consists in pursuing the goal that will launch the system, and then patching any reported holes (bugs).
VirtIO disk reading is working. Boot volume is mounted.
device 0: /dev/disk/virtual/virtio_block/0/raw
media status: No error
device flags: 2
offset: 0
size: 314573312 (300 MB)
content size: 314572800
block size: 2048
child count: 0
index: -1
status: 0
flags: 3
volume: -1
disk system: file_systems/bfs/v1
name: <NULL>
content name: Haiku
type: <NULL>
content type: Be File System
params: <NULL>
content params: <NULL>
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x810598c0, 0x200, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x810598c0, 0x200, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x810598c0, 0x200, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x810598c0, 0x200, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x810598c0, 0x200, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
Identified boot partition by partition offset.
virtio_block: CALLED status_t virtio_block_open(void*, const char*, int, void**)
virtio_block: CALLED status_t virtio_block_ioctl(void*, uint32, void*, size_t)
virtio_block: ioctl(op = 7)
virtio_block: virtio_block: get_geometry(): 512, 614401, 1, 1, 0, 0, 0, 0
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff7b0, 0x10, read
vector[1]: 0x81059400, 0x400, write
vector[2]: 0x812ff7c0, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_ioctl(void*, uint32, void*, size_t)
virtio_block: ioctl(op = 7)
virtio_block: virtio_block: get_geometry(): 512, 614401, 1, 1, 0, 0, 0, 0
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff420, 0x10, read
vector[1]: 0x818e7800, 0x800, write
vector[2]: 0x812ff430, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff420, 0x10, read
vector[1]: 0x818e6800, 0x800, write
vector[2]: 0x812ff430, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff420, 0x10, read
vector[1]: 0x818e5800, 0x800, write
vector[2]: 0x812ff430, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_block: CALLED status_t virtio_block_read(void*, off_t, void*, size_t*)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff420, 0x10, read
vector[1]: 0x818e4800, 0x800, write
vector[2]: 0x812ff430, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_request_v(0x00000000813b7cb0)
vector[0]: 0x812ff420, 0x10, read
vector[1]: 0x812b8000, 0x800, write
vector[2]: 0x812ff430, 0x1, write
virtio_mmio: dev->fRegs->queueNotify = 0
TinyEMU: queue_notify(0)
TinyEMU: virtio_block_recv_request
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
bfs: mounted "Haiku" (root node at 131072, device = /dev/disk/virtual/virtio_block/0/raw)
Mounted boot partition: /dev/disk/virtual/virtio_block/0/raw
Currently loading stops here. Illegal instruction in strtoull()? What? Lets go disassembling again with my disassembler 
STrap(interrupt sExtern)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sie: {sExtern}
sip: {sExtern}
irq: 3
Stack:
FP: 0xcd11fce0, PC: <kernel_riscv64> STrap + 363
FP: 0xcd11fde0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fe60, PC: <virtio_block> _ZL5do_ioPvP11IOOperation + 229
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1181
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
virtio_mmio: virtio_interrupt_handler(0x0000000081265600)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
virtio_mmio: virtio_device_queue_dequeue(0x00000000810241e0)
STrap(exception illegalInst)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <kernel_riscv64> strtoull.localalias.0 + 212
sie: {sExtern}
sip: {}
PANIC: unhandled STrap
Welcome to Kernel Debugging Land...
Thread 14 "main2" running on CPU 0
Stack:
FP: 0xcd099090, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0xcd099100, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0xcd099140, PC: <kernel_riscv64> panic + 93
FP: 0xcd099280, PC: <kernel_riscv64> SVec + 81
FP: 0xcd099330, PC: <kernel_riscv64> strtoull.localalias.0 + 211
FP: 0xcd0994a0, PC: <kernel_riscv64> load_driver_settings + 157
FP: 0xcd0994d0, PC: <kernel_riscv64> _ZL10get_optionP11kernel_argsPKcS2_mPcPm.part.2 + 25
FP: 0xcd099510, PC: <kernel_riscv64> _ZL11get_booleanP11kernel_argsPKcb + 33
FP: 0xcd0996c0, PC: <kernel_riscv64> legacy_driver_probe + 1315
FP: 0xcd099720, PC: <kernel_riscv64> _ZL26scan_for_drivers_if_neededPN12_GLOBAL__N_111devfs_vnodeE + 239
FP: 0xcd099760, PC: <kernel_riscv64> _ZL12devfs_lookupP9fs_volumeP8fs_vnodePKcPl + 51
FP: 0xcd0997a0, PC: <kernel_riscv64> _ZL16lookup_dir_entryP5vnodePKcPS0_ + 105
FP: 0xcd099870, PC: <kernel_riscv64> _ZL19vnode_path_to_vnodeP5vnodePcbiP10io_contextPS0_Pl + 475
FP: 0xcd0998a0, PC: <kernel_riscv64> _ZL21common_path_read_statiPcbP4statb + 25
FP: 0xcd099900, PC: <kernel_riscv64> vfs_read_stat.localalias.7 + 73
FP: 0xcd0999b0, PC: <kernel_riscv64> _kern_read_stat + 69
FP: 0xcd0999d0, PC: <kernel_riscv64> _lstat_current.localalias.1 + 25
FP: 0xcd099ac0, PC: <kernel_riscv64> _ZN8BPrivate10DiskDevice18KDiskDeviceManager5_ScanEPKc.localalias.5 + 49
FP: 0xcd099b10, PC: <kernel_riscv64> _ZN8BPrivate10DiskDevice18KDiskDeviceManager17InitialDeviceScanEv.localalias.13 + 161
FP: 0xcd099b30, PC: <kernel_riscv64> _ZN8BPrivate10DiskDevice18KDiskDeviceManager15StartMonitoringEv + 15
FP: 0xcd099f70, PC: <kernel_riscv64> vfs_mount_boot_file_system + 1119
FP: 0xcd099fc0, PC: <kernel_riscv64> _ZL5main2Pv + 283
FP: 0xcd099fe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
kdebug>
Mysterious exception in <kernel_riscv64> strtoull.localalias.0 + 215 continue to occurr in different places.
strtoull
8013BFEC 7179 ADDI SP, SP, -48
8013BFEE F022 SD FP, 32(SP)
8013BFF0 E44E SD S3, 8(SP)
8013BFF2 E052 SD S4, 0(SP)
8013BFF4 F406 SD RA, 40(SP)
8013BFF6 EC26 SD S1, 24(SP)
8013BFF8 E84A SD S2, 16(SP)
8013BFFA 1800 ADDI FP, SP, 48
8013BFFC 6797 0004 AUIPC A5, $00046000
8013C000 B783 71C7 LD A5, __imp___ctype_b
8013C004 89AA MV S3, A0
8013C006 86AA MV A3, A0
8013C008 8A2E MV S4, A1
8013C00A B803 0007 LD A6, 0(A5)
8013C00E 6509 LUI A0, $00002000
8013C010 A011 J $8013C014
8013C012 86A6 MV A3, S1
8013C014 8493 0016 ADDI S1, A3, 1
8013C018 C703 FFF4 LBU A4, -1(S1)
8013C01C 1793 0017 SLLI A5, A4, 1
8013C020 97C2 ADD A5, A6
8013C022 D783 0007 LHU A5, 0(A5)
8013C026 8FE9 AND A5, A5, A0
8013C028 F7ED BNEZ A5, $8013C012
8013C02A 0793 02D0 LI A5, 45
8013C02E 0D63 0EF7 BEQ A4, A5, $8013C128
8013C032 0793 02B0 LI A5, 43
8013C036 4301 LI T1, 0
8013C038 0563 0AF7 BEQ A4, A5, $8013C0E2
8013C03C E635 BNEZ A2, $8013C0A8
8013C03E 0793 0300 LI A5, 48
8013C042 0463 14F7 BEQ A4, A5, $8013C18A
8013C046 7797 0002 AUIPC A5, $00027000
8013C04A 8793 3927 LI A5, $801633D8
8013C04E 638C LD A1, 0(A5)
8013C050 4E15 LI T3, 5
8013C052 48A9 LI A7, 10
8013C054 4629 LI A2, 10
8013C056 4681 LI A3, 0
8013C058 4901 LI S2, 0
8013C05A 4525 LI A0, 9
8013C05C 4865 LI A6, 25
8013C05E A829 J $8013C078
8013C060 56FD LI A3, -1
8013C062 E863 0125 BLTU A1, S2, $8013C072
8013C066 0E63 0AB9 BEQ S2, A1, $8013C122
8013C06A 8933 0328 MUL S2, A7, S2
8013C06E 4685 LI A3, 1
8013C070 993E ADD S2, A5
8013C072 0485 ADDI S1, S1, 1
8013C074 C703 FFF4 LBU A4, -1(S1)
8013C078 079B FD07 ADDIW A5, A4, -48
8013C07C F793 0FF7 ANDI A5, A5, 255
8013C080 7C63 00F5 BBGEU A0, A5, $8013C098
8013C084 079B FBF7 ADDIW A5, A4, -65
8013C088 F793 0FF7 ANDI A5, A5, 255
8013C08C 6163 06F8 BLTU A6, A5, $8013C0EE
8013C090 079B FC97 ADDIW A5, A4, -55
8013C094 F793 0FF7 ANDI A5, A5, 255
8013C098 871B 0007 ADDIW A4, A5, 0
8013C09C 5763 06C7 BGE A4, A2, $8013C10A
8013C0A0 D0E3 FC06 BGE A3, 0, $8013C060
8013C0A4 56FD LI A3, -1
8013C0A6 B7F1 J $8013C072
8013C0A8 47C1 LI A5, 16
8013C0AA 0F63 08F6 BEQ A2, A5, $8013C148
8013C0AE 079B FFE6 ADDIW A5, A2, -2
8013C0B2 0693 0220 LI A3, 34
8013C0B6 F863 0EF6 BBGEU A3, A5, $8013C1A6
8013C0BA 80EF 9872 JAL _errnop
8013C0BE 07B7 8000 LUI A5, $80000000
8013C0C2 2795 LI A5, $80000005
8013C0C4 C11C SW A5, 0(A0) (* <--- TRAPS HERE *)
8013C0C6 4901 LI S2, 0
8013C0C8 0463 000A BEQ S4, 0, $8013C0D0
8013C0CC 3023 013A SD S3, 0(S4)
8013C0D0 70A2 LD RA, 40(SP)
8013C0D2 7402 LD FP, 32(SP)
8013C0D4 854A MV A0, S2
8013C0D6 64E2 LD S1, 24(SP)
8013C0D8 6942 LD S2, 16(SP)
8013C0DA 69A2 LD S3, 8(SP)
8013C0DC 6A02 LD S4, 0(SP)
8013C0DE 6145 ADDI SP, SP, 48
8013C0E0 8082 RET
What is the value of A0? I don’t know about RISC-V but on other architectures I’ve had “illegal instruction” because of misaligned memory access.
One of possible causes may be old kernel module binaries in disk image. Replacing it seems to fix issue, but hit next old module. I try to rebuild whole disk image.
Compiler flags and common headers was changed since last disk image generation.
Problem is still present after recompiling everything:
STrap(exception storePageFault)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <kernel_riscv64> strtoull.localalias.0 + 216
sie: {sExtern}
sip: {}
stval: 0x2
PANIC: unhandled STrap
Welcome to Kernel Debugging Land...
Thread 14 "main2" running on CPU 0
Stack:
FP: 0xcd0999d0, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0xcd099a40, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0xcd099a80, PC: <kernel_riscv64> panic + 93
FP: 0xcd099bc0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd099ca0, PC: <kernel_riscv64> strtoull.localalias.0 + 215
FP: 0xcd099cb0, PC: <iso9660> 0x1219
FP: 0xcd099de0, PC: <kernel_riscv64> get_module.localalias.1 + 1069
FP: 0xcd099f70, PC: <kernel_riscv64> debug_init_post_modules + 329
FP: 0xcd099fc0, PC: <kernel_riscv64> _ZL5main2Pv + 371
FP: 0xcd099fe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
kdebug>
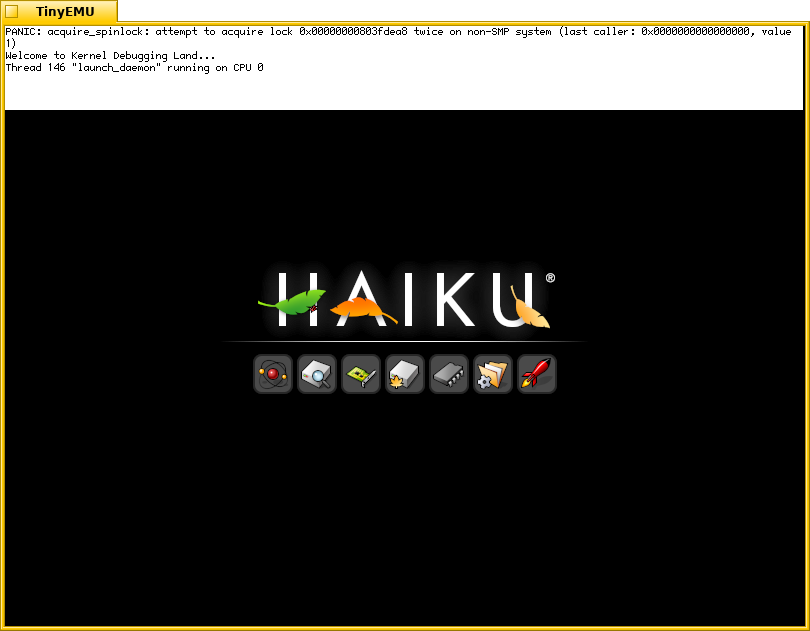
I just disabled dynamic loading of kernel add-ons and loading progressed to rocket icon! Even first userland process “launch_daemon” is visible in KDL. Userland is almost not implemened so it is not expected to run. Currently is infinitely crash without stack trace.
Dynamic loading of kernel add-ons seems not working correctly, probably someting is not implemented (relocations types etc.). Modules preloaded by boot loader are fine.
Out of curiosity what needs to be implemented here for userland to work?
I have not yet investigated exactly, but at least following is needed:
- Switch thread to user mode.
- Change address space when switching thread.
- Handle traps with mode change. Trap in user land should switch to kernel land and kernel address space/stack.
- Implement
user_memcpy()etc. Currently it just wrapsmemcpy()etc. - Implement syscalls. Currently only special machine-mode syscalls are supported (needed to control timer but currently also used to switch to supervisor mode).
- Probably improve RISCV64VMTranslationMap.
-
commpagestuff.
I fixed some problems, now it crash when attempting to copy memory to userland (user_strlcpy). High addresses are currently used for userland, for example 0xffffffed13a66220.
arch_thread_init_kthread_stack(0x000000008129afc0(launch_daemon), 0x0000000080b2d000, 0x0000000080b31fb0, <kernel_riscv64> _ZL19common_thread_entryPv + 0, 0x0000000080b31fb0)
(24)
(25)
(26)
(27)
(28)
arch_thread_context_switch(0x000000008129be00(main2), 0x000000008129afc0(launch_daemon))
STrap(exception storePageFault)
sstatus: (ie: {}, pie: {s}, spp: s)
sepc: <kernel_riscv64> strlcpy + 46
sie: {sExtern}
sip: {}
stval: 0xffffffed13a66220
Stack:
FP: 0x80b31950, PC: <kernel_riscv64> STrap + 409
FP: 0x80b31a50, PC: <kernel_riscv64> SVec + 81
FP: 0x80b31a70, PC: <kernel_riscv64> strlcpy + 45
FP: 0x80b31a90, PC: <kernel_riscv64> user_strlcpy.localalias.17 + 79
FP: 0x80b31f80, PC: <kernel_riscv64> _ZL33team_create_thread_start_internalPv + 125
FP: 0x80b31f90, PC: <kernel_riscv64> _ZL24team_create_thread_startPv + 11
FP: 0x80b31fb0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
PANIC: unhandled STrap
Welcome to Kernel Debugging Land...
Thread 146 "launch_daemon" running on CPU 0
Stack:
FP: 0x80b31860, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0x80b318d0, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0x80b31910, PC: <kernel_riscv64> panic + 93
FP: 0x80b31a50, PC: <kernel_riscv64> SVec + 81
FP: 0x80b31a70, PC: <kernel_riscv64> strlcpy + 45
FP: 0x80b31a90, PC: <kernel_riscv64> user_strlcpy.localalias.17 + 79
FP: 0x80b31f80, PC: <kernel_riscv64> _ZL33team_create_thread_start_internalPv + 125
FP: 0x80b31f90, PC: <kernel_riscv64> _ZL24team_create_thread_startPv + 11
FP: 0x80b31fb0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
Great progress, please continue!
Implemented and fixed parts up to arch_thread_enter_userspace (). runtime_loader is loaded.
Welcome to Kernel Debugging Land...
Thread 146 "launch_daemon" running on CPU 0
Stack:
FP: 0x80b348f0, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0x80b34960, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0x80b349a0, PC: <kernel_riscv64> panic + 93
FP: 0x80b349f0, PC: <kernel_riscv64> arch_thread_enter_userspace + 19
FP: 0x80b34a30, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 135
FP: 0x80b34a90, PC: <kernel_riscv64> thread_enter_userspace_new_team + 53
FP: 0x80b34f80, PC: <kernel_riscv64> _ZL33team_create_thread_start_internalPv + 681
FP: 0x80b34f90, PC: <kernel_riscv64> _ZL24team_create_thread_startPv + 11
FP: 0x80b34fb0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
kdebug>
Maybe it help you
runtime_loader is executing in user mode!
execPageFault occurs because executable is memory mapped file and it is dynamically loaded from disk by page fault handler vm_page_fault().
arch_thread_enter_uspace(0x000000008129afc0(launch_daemon), 0xffffffecea269418, 0xffffffed13a66200, 0xffffffe99170e000)
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0x11418
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0x11418
Stack:
FP: 0xffffffed13a65f00, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a66000, PC: <kernel_riscv64> SVec + 81
FP: 0x80b33a30, PC: </boot/system/runtime_loader> 0x11417
FP: 0x80b33a90, PC: <kernel_riscv64> thread_enter_userspace_new_team + 53
FP: 0x80b33f80, PC: <kernel_riscv64> _ZL33team_create_thread_start_internalPv + 547
FP: 0x80b33f90, PC: <kernel_riscv64> _ZL24team_create_thread_startPv + 11
FP: 0x80b33fb0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0xa940
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0xa940
Stack:
FP: 0xffffffed13a65ed0, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a65fd0, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffecea2733d0, PC: </boot/system/runtime_loader> 0xa93f
FP: 0x0, PC: 0xffffffe99170dfff
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0xea2e
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0xea2e
Stack:
FP: 0xffffffed13a65ed0, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a65fd0, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffecea2733d0, PC: </boot/system/runtime_loader> 0xea2d
FP: 0x0, PC: 0xffffffe99170dfff
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0x135b0
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0x135b0
Stack:
FP: 0xffffffed13a65e60, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a65f60, PC: <kernel_riscv64> SVec + 81
FP: 0x10000, PC: </boot/system/runtime_loader> 0x135af
STrap(exception loadPageFault)
sstatus: (ie: {u}, pie: {}, spp: s, fs: 3, sum: 1)
sepc: <kernel_riscv64> arch_debug_stack_trace + 58
sie: {sExtern}
sip: {}
stval: 0xfff8
Stack:
FP: 0xffffffed13a65cd0, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a65dd0, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65e10, PC: <kernel_riscv64> arch_debug_stack_trace + 57
FP: 0xffffffed13a65e60, PC: <kernel_riscv64> STrap + 447
FP: 0xffffffed13a65f60, PC: <kernel_riscv64> SVec + 81
FP: 0x10000, PC: </boot/system/runtime_loader> 0x135af
Address decoding:
</boot/system/runtime_loader> 0x11418: runtime_loader (entry point)
</boot/system/runtime_loader> 0xa940: heap_init (PLT stub)
</boot/system/runtime_loader> 0xea2e: heap_init
</boot/system/runtime_loader> 0x135b0: _kern_generic_syscall
All syscalls points here. Syscalls seems to be not implemented.
_kern_generic_syscall
001135B0 0000 ADDI FP, SP, 0
001135B2 0000 ADDI FP, SP, 0
001135B4 0000 ADDI FP, SP, 0
001135B6 0000 ADDI FP, SP, 0
001135B8 0000 ADDI FP, SP, 0
001135BA 0000 ADDI FP, SP, 0
001135BC 0000 ADDI FP, SP, 0
Userland process is invoking syscall in kernel (_kern_create_area):
arch_thread_enter_uspace(0x000000008129afc0(launch_daemon), 0xffffffd4456f0418, 0xffffffed13a66200, 0xffffffe99170e000)
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0x11418
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0x11418
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0xa940
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0xa940
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0xea2e
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0xea2e
STrap(exception execPageFault)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0x141c0
sie: {sExtern}
sip: {}
stval: </boot/system/runtime_loader> 0x141c0
STrap(exception uEcall)
sstatus: (ie: {u}, pie: {s}, spp: u, fs: 3, sum: 1)
sepc: </boot/system/runtime_loader> 0x141c4
sie: {sExtern}
sip: {}
syscall 193(_kern_create_area)
Power off.
So cool!! Thank you for these updates 
Syscalls are basically working, but user trap frame (trap frames are called iframes in haiku kernel code) is currently pushed on user stack and syscall handler is running on user stack. That cause crash when kernel thread atemts to read object on stack created on syscall handler stack. Some special handling is needed for user -> kernel traps so stack will be immitiately switched to kernel stack and trap frame fill be pushed there.
arch_thread_enter_uspace(0x000000008129b400(launch_daemon), 0xfffffff214c56c22, 0xffffffed13a66200, 0xffffffe99170e000)
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0x11c22
sepc: 0xfffffff214c56c22
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x11c22
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0xa2f0
sepc: 0xfffffff214c4f2f0
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0xa2f0
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0x152a0
sepc: 0xfffffff214c5a2a0
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x152a0
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x152a4
sepc: 0xfffffff214c5a2a4
sie: {sExtern}
sip: {}
syscall 245(_kern_debug_output)
Stack:
FP: 0xffffffed13a65ec0, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a65fc0, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x152a3
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
STrap(exception loadPageFault)
sepc: <kernel_riscv64> strlcpy + 18
sepc: 0x0000000080395698
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x18c48
runtime_loader entry point
syscall_dispatcher: done with syscall 0xf5
syscall 245(_kern_debug_output) result: 0
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x152a4
sepc: 0xfffffff214c5a2a4
sie: {sExtern}
sip: {}
syscall 245(_kern_debug_output)
Stack:
FP: 0xffffffed13a65ec0, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a65fc0, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x152a3
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
(1)
syscall_dispatcher: done with syscall 0xf5
syscall 245(_kern_debug_output) result: 0
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0xefd0
sepc: 0xfffffff214c53fd0
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0xefd0
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0x14f60
sepc: 0xfffffff214c59f60
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x14f60
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x14f64
sepc: 0xfffffff214c59f64
sie: {sExtern}
sip: {}
syscall 193(_kern_create_area)
Stack:
FP: 0xffffffed13a65e40, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a65f40, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0x14f63
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11cd7
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
syscall_dispatcher: done with syscall 0xc1
syscall 193(_kern_create_area) result: 346
STrap(exception storePageFault)
sepc: <runtime_loader_seg0ro> 0xec52
sepc: 0xfffffff214c53c52
sie: {sExtern}
sip: {}
stval: <rld heap> 0x0
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0x10c58
sepc: 0xfffffff214c55c58
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x10c58
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0xc2ea
sepc: 0xfffffff214c512ea
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0xc2ea
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x14f64
sepc: 0xfffffff214c59f64
sie: {sExtern}
sip: {}
syscall 193(_kern_create_area)
Stack:
FP: 0xffffffed13a65e90, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a65f90, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0x14f63
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11ce5
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
syscall_dispatcher: done with syscall 0xc1
syscall 193(_kern_create_area) result: 347
STrap(exception storePageFault)
sepc: <runtime_loader_seg0ro> 0xc326
sepc: 0xfffffff214c51326
sie: {sExtern}
sip: {}
stval: <_rld_debug_> 0x0
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0xb67a
sepc: 0xfffffff214c5067a
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0xb67a
STrap(exception execPageFault)
sepc: <runtime_loader_seg0ro> 0x16c2e
sepc: 0xfffffff214c5bc2e
sie: {sExtern}
sip: {}
stval: <runtime_loader_seg0ro> 0x16c2e
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x14674
sepc: 0xfffffff214c59674
sie: {sExtern}
sip: {}
syscall 50(_kern_find_thread)
Stack:
FP: 0xffffffed13a65e40, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a65f40, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65f60, PC: <runtime_loader_seg0ro> 0x14673
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0xb699
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11cf5
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
syscall_dispatcher: done with syscall 0x32
syscall 50(_kern_find_thread) result: 146
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x14a04
sepc: 0xfffffff214c59a04
sie: {sExtern}
sip: {}
syscall 107(_kern_open)
Stack:
FP: 0xffffffed13a64510, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a64610, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a64a60, PC: <runtime_loader_seg0ro> 0x14a03
FP: 0xffffffed13a65f60, PC: <runtime_loader_seg0ro> 0xcacb
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0xb6b3
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11cf5
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
syscall_dispatcher: done with syscall 0x6b
syscall 107(_kern_open) result: 0
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x149e4
sepc: 0xfffffff214c599e4
sie: {sExtern}
sip: {}
syscall 105(_kern_normalize_path)
Stack:
FP: 0xffffffed13a64960, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a64a60, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65f60, PC: <runtime_loader_seg0ro> 0x149e3
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0xb6b3
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11cf5
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
syscall_dispatcher: done with syscall 0x69
syscall 105(_kern_normalize_path) result: 0
STrap(exception uEcall)
sepc: <runtime_loader_seg0ro> 0x14c34
sepc: 0xfffffff214c59c34
sie: {sExtern}
sip: {}
syscall 142(_kern_read)
Stack:
FP: 0xffffffed13a64960, PC: <kernel_riscv64> STrap + 327
FP: 0xffffffed13a64a60, PC: <kernel_riscv64> SVec + 81
FP: 0xffffffed13a65f60, PC: <runtime_loader_seg0ro> 0x14c33
FP: 0xffffffed13a65fc0, PC: <runtime_loader_seg0ro> 0xb6b3
FP: 0xffffffed13a66000, PC: <runtime_loader_seg0ro> 0x11cf5
FP: 0x0, PC: <kernel_riscv64> _ZL15enter_userspacePN7BKernel6ThreadEP24UserThreadEntryArguments + 67
STrap(interrupt sExtern)
sepc: <virtio_block> _ZL5do_ioPvP11IOOperation + 230
sepc: 0x00000000809e85ac
sie: {sExtern}
sip: {sExtern}
STrap(exception loadPageFault)
sepc: <kernel_riscv64> _ZNK9IORequest12HasCallbacksEv.localalias.8 + 6
sepc: 0x00000000803325ce
sie: {sExtern}
sip: {}
stval: 0xffffffed13a642f8
vm_page_fault: kernel thread accessing invalid user memory!
vm_page_fault: vm_soft_fault returned error 'Bad address' on fault at 0xffffffed13a642f8, ip 0x803325ce, write 0, user 0, thread 0x8e
PANIC: vm_page_fault: unhandled page fault in kernel space at 0xffffffed13a642f8, ip 0x803325ce
Welcome to Kernel Debugging Land...
Thread 142 "virtio scheduler 1" running on CPU 0
Stack:
FP: 0xcd11faa0, PC: <kernel_riscv64> _ZL20kernel_debugger_loopPKcS0_Pvi + 243
FP: 0xcd11fb10, PC: <kernel_riscv64> _ZL24kernel_debugger_internalPKcS0_Pvi + 131
FP: 0xcd11fb50, PC: <kernel_riscv64> panic + 93
FP: 0xcd11fc80, PC: <kernel_riscv64> vm_page_fault + 425
FP: 0xcd11fcc0, PC: <kernel_riscv64> STrap + 753
FP: 0xcd11fdc0, PC: <kernel_riscv64> SVec + 81
FP: 0xcd11fdd0, PC: <kernel_riscv64> _ZNK9IORequest12HasCallbacksEv.localalias.8 + 5
FP: 0xcd11fe60, PC: 0xcd11fe5f
FP: 0xcd11ffc0, PC: <kernel_riscv64> _ZN17IOSchedulerSimple10_SchedulerEv.localalias.2 + 1187
FP: 0xcd11ffe0, PC: <kernel_riscv64> _ZL19common_thread_entryPv + 49
FP: 0x0, PC: <kernel_riscv64> arch_thread_entry + 3